In the cloud era, security and efficiency are paramount. One common challenge faced by organizations is managing secure access to EC2 instances. Traditional methods like SSH require manual key management, which can lead to risks like leaked keys or unauthorized access. Amazon EC2 Instance Connect Endpoint offers a secure and efficient alternative, eliminating the need for SSH while enhancing security and simplifying access. Here’s everything you need to know to get started and avoid the pitfalls of traditional SSH-based access.
What Is EC2 Instance Connect Endpoint?
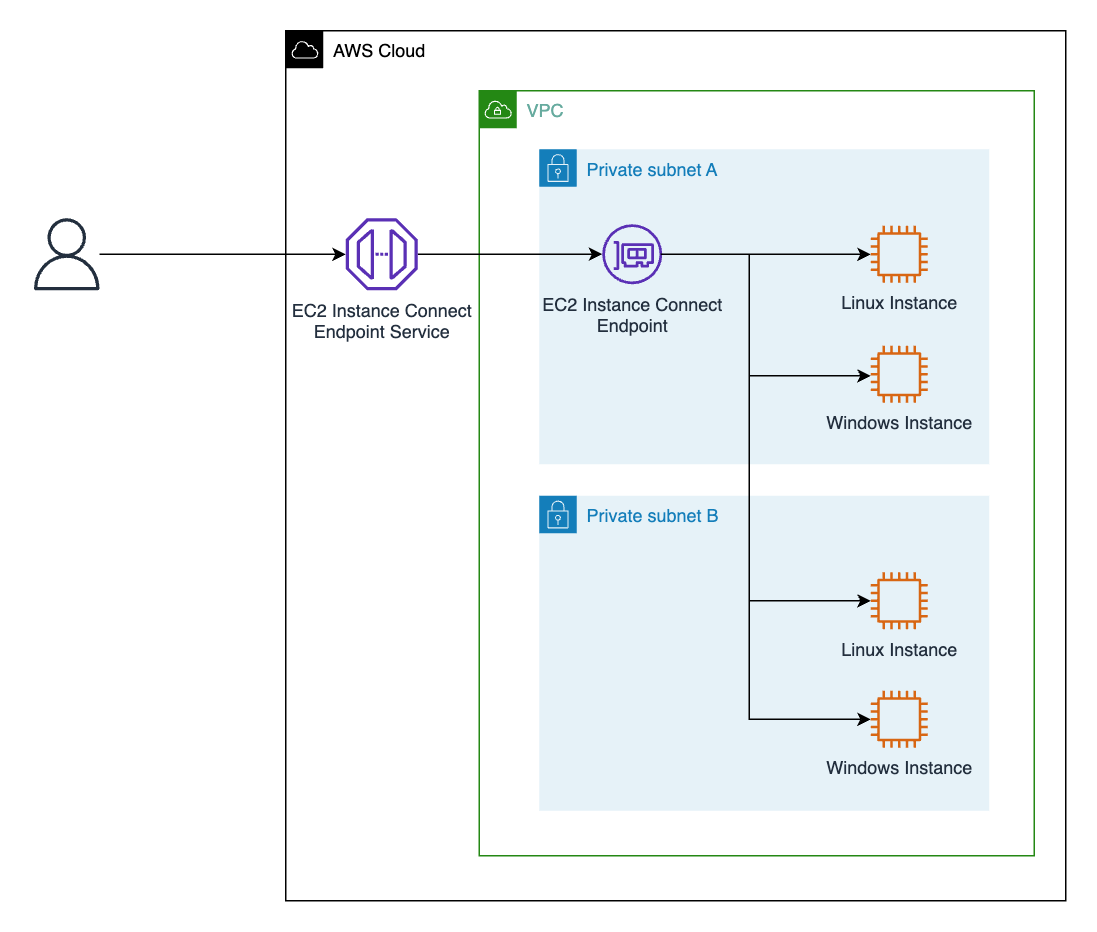
EC2 Instance Connect Endpoint is an AWS feature that allows you to securely access instances in your VPC without managing SSH keys. It eliminates the need for direct SSH access, enabling temporary key injection for secure authentication.
How It Works
- EC2 Instance Connect Endpoint creates a network interface in a specific subnet.
- Users send requests through the endpoint to connect to instances in the same or other subnets, provided the route tables allow it.
- Temporary SSH keys are injected directly into the instance without manual configuration.
Why Avoid Traditional SSH?
Traditional SSH access comes with challenges:
- Key Management Overhead: Sharing, rotating, and revoking SSH keys can be a manual and error-prone process.
- Security Risks: Lost or leaked private keys pose significant risks.
- Network Exposure: Instances often require public IPs and open port 22, increasing the attack surface.
By using EC2 Instance Connect Endpoint, you can address these issues effectively.
Benefits of Using EC2 Instance Connect Endpoint
- No SSH Key Management
Temporary keys are injected during each session, eliminating the need to maintain permanent keys. - Enhanced Security
- No need to open port 22 to the internet.
- Instances can remain in private subnets with no public IPs.
- Seamless IAM Integration
Permissions for access are tied to IAM policies, offering granular control. - Centralized Access Control
Use AWS Identity and Access Management (IAM) to govern who can connect to which instances, simplifying auditing and compliance.
Step-by-Step Guide to Setting Up EC2 Instance Connect Endpoint
1. Create an EC2 Instance Connect Endpoint
- Navigate to the VPC Console > Endpoints.
- Choose Create Endpoint.
- Select the com.amazonaws.<region>.ec2-instance-connect service.
- Choose the VPC and subnet where the endpoint will be created.
- Attach a security group that allows traffic to your instances.
2. Configure Security Groups
For the Endpoint: The security group rules for an EC2 Instance Connect Endpoint must allow outbound traffic destined for the target instances to leave the endpoint. You can specify either the instance security group or the IPv4 address range of the VPC as the destination.

For the Instance: The security group rules for target instances must allow inbound traffic from the EC2 Instance Connect Endpoint. You can specify either the endpoint security group or an IPv4 address range as the source. If you specify an IPv4 address range, the source depends on whether client IP preservation is off or on. For more information, see Considerations.

Reference: Configure Security Groups
3. Install Required Packages
For EC2 Instance Connect to work, supported operating systems (Amazon Linux 2, Ubuntu 20.04+) must have the ec2-instance-connect package installed.
Install it if missing:
sudo yum install ec2-instance-connect -y # Amazon Linux 2
sudo apt-get install ec2-instance-connect -y # Ubuntu
4. Set Up IAM Policies
Attach an IAM role to the instance with the following permissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ec2-instance-connect:SendSSHPublicKey"
],
"Resource": "arn:aws:ec2:<region>:<account-id>:instance/<instance-id>"
}
]
}Troubleshooting Common Issues
1: Permission Denied (publickey)
- Ensure the
ec2-instance-connectpackage is installed. - Verify IAM permissions and roles attached to the instance.
2: Unsupported Operating System
- Use supported AMIs like Amazon Linux 2 or Ubuntu 20.04+.
- For unsupported OS, manually add public keys to
~/.ssh/authorized_keys.
3: Misconfigured Security Groups
- Ensure SSH (port 22) is open for the Instance Connect Endpoint’s subnet.
Best Practices for Using EC2 Instance Connect Endpoint
- Use Private Subnets
Keep your instances in private subnets and access them through the endpoint. - Leverage IAM Policies
Use least-privilege principles to restrict who can access specific instances. - Automate Package Installation
For new instances, automate the installation ofec2-instance-connectusing AWS Systems Manager or instance launch templates. - Monitor Access Logs
Use AWS CloudTrail to track EC2 Instance Connect requests for audit and compliance.
Leave a Reply